Information Security and Risk Management: Identify and Eliminate Your IT and Security Risks
Risk comes in many forms for technology-driven organizations. EMBER’s Information Security and Risk Management solution offers a comprehensive, proactive approach to managing security technology planning, compliance, and security awareness.
A Proven Approach to Risk Mitigation
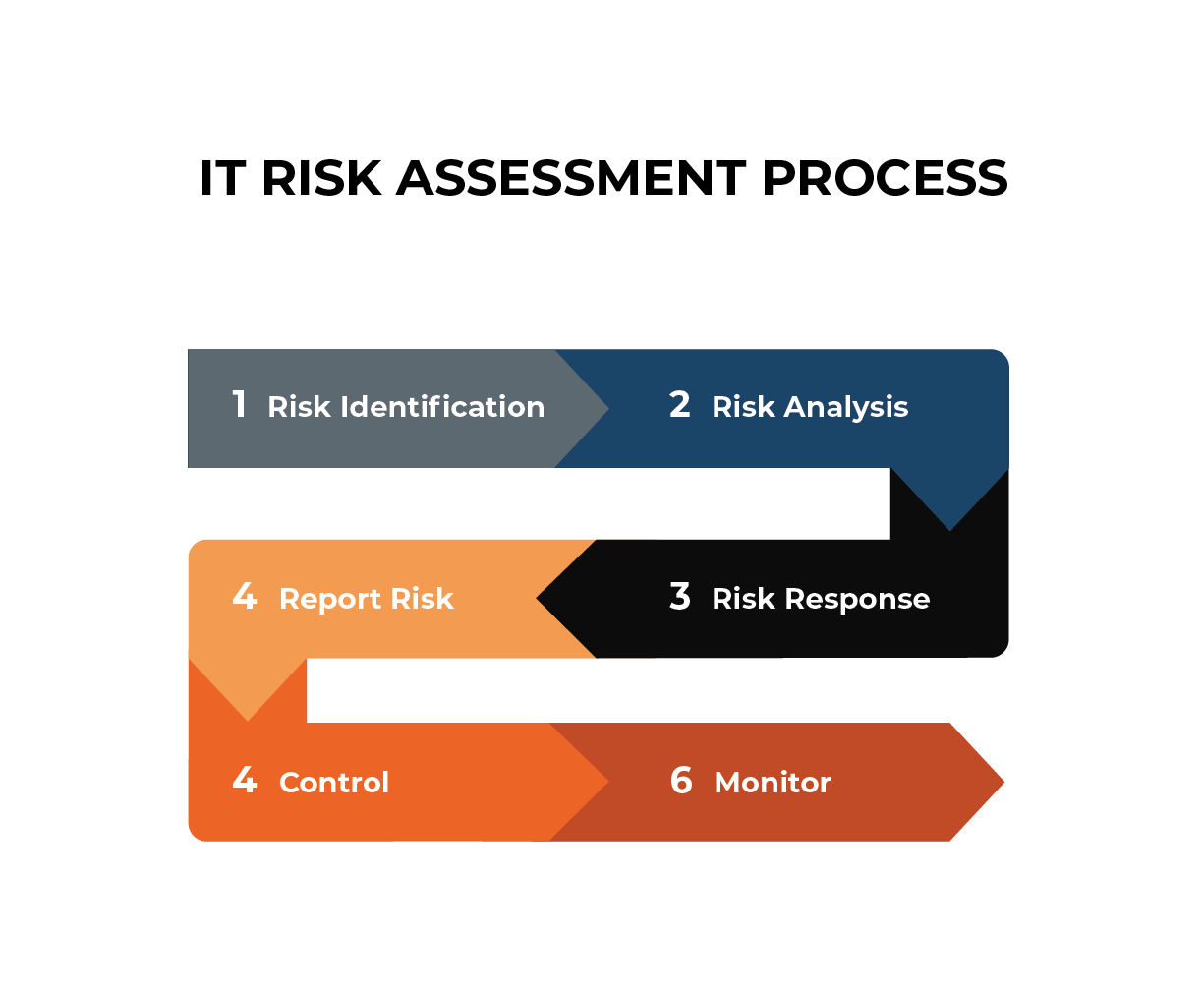
You need to identify and address security and compliance risks before they impact your business. EMBER’s five-step approach to Information Security and Risk Management assesses your current environment and infrastructure, then creates and implements a comprehensive strategy to eliminate potential threats.

EMBER’s Information Security and Risk Management:
EMBER’s Information Security and Risk Management solution utilizes a proven playbook to eliminate vulnerabilities and reduce risk in your environment. We employ a five-step framework — Protect, Identify, Detect, Respond, and Recover.
The EMBER team will
- Identify your organization’s digital assets
- Review existing security measures
- Call out potential security gaps and vulnerabilities
- Create and implement proactive security and response plans
- Conduct ongoing audits and reporting to ensure optimal performance
Tools We Use to Manage Information Security and Risk Management
EMBER Strategic Technology Consulting —
Partnering for Your Success
EMBER’s technology experts use industry-leading tools and best practices to discover, assess, and solve your most complex IT challenges, including
- Evaluating your current IT landscape
- Building your long-term technology roadmap
- Developing industry-specific technology solutions
- Planning and executing complex hardware and applications rollouts
- Creating a resilient security infrastructure